AT88SC3216CRF-MVB1G Atmel, AT88SC3216CRF-MVB1G Datasheet - Page 122

AT88SC3216CRF-MVB1G
Manufacturer Part Number
AT88SC3216CRF-MVB1G
Description
CRYPTOMEMORY 32KBIT 16ZONE MVB
Manufacturer
Atmel
Series
CryptoMemory®, CryptoRF®r
Datasheets
1.AT88RF04C-MVB1G.pdf
(158 pages)
2.AT88RF04C-MVB1G.pdf
(2 pages)
3.AT88SC3216CRF-MR1.pdf
(9 pages)
Specifications of AT88SC3216CRF-MVB1G
Rf Type
Read / Write
Frequency
13.56MHz
Features
ISO1444-2, 1444-3, 32-kbits
Package / Case
MVB Module
Lead Free Status / RoHS Status
Lead free / RoHS Compliant
- Current page: 122 of 158
- Download datasheet (892Kb)
K.8.
122
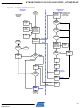
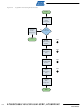
Encryption Activation
Authentication Activation must be performed prior to Encryption Activation. The Mutual Authentication is performed in
steps 1 thru 7, and Encryption Activation in steps 8 thru 11 of the following procedure.
1.
2.
3.
4.
5.
6.
7.
8.
9.
10. The PICC calculates challenge CH and other parameters using QE from the host with the cryptographic engine:
11. The PICC compares the internally calculated challenge CH to the value received from the host. If CH = CHE then
The Secret Seed G
are written (by the PICC) each time a Verify Crypto command is received by the PICC. The S
PICC) each time the Mutual Authentication procedure succeeds.
If the Host receives a NACK response from the PICC, then the Mutual Authentication procedure can be retried starting
with step 2.
Figure 35 shows the Authentication Activation procedure as a flowchart. Figure 39 shows the Encryption Activation
procedure as a flowchart.
AT88SC0808/1616/3216/6416CRF, AT88RF04C
The Host reads the PICC ID from Nc (or another equivalent memory location) and calculates the diversified key
matching the PICC Secret Seed G. G = F1(K, ID, x, y, z)
The Host reads AACi and Ci from card.
The Host generates a Random Number QA and calculates challenge CHA and other parameters with the
cryptographic engine: [CHA, CA, SA] = F2(G, C, QA)
The Host Sends Verify Crypto Command with Key Index $0i: Verify Crypto ($0i, QA, CHA)
The PICC calculates challenge CH and other parameters using QA from the host with the cryptographic engine:
[CH, CiA, SiA] = F2(Gi, Ci, QA)
The PICC compares the internally calculated challenge CH to the value received from the host. If CH = CHA then
the host is authenticated and the card writes the calculated values of CiA to the Ci register and SiA to the Si
register. The AACi is cleared, Authentication Communication Security mode is activated, and an ACK response is
returned to the host.
The Host reads the new AACi and CiA from Ci register of the PICC and compares it to the calculated CA from step
3. If CA = CiA then the card is authenticated. The Mutual Authentication procedure is complete.
The Host generates a Random Number QE and calculates challenge CHE and other parameters with the
cryptographic engine: [CHE, CE] = F2(SiA, CiA, QE)
The Host Sends Verify Crypto Command with Key Index $1i: Verify Crypto ($1i, QE, CHE)
[CH, CiE] = F2(SiA, CiA, QE)
the host is authenticated and the card writes the calculated value of CiE to the Ci register. The AACi is cleared,
Encryption Communication Security mode is activated, and an ACK response is returned to the host.
i
value in the PICC never changes after it is locked at personalization. The AAC
i
register is written (by the
i
, and C
5276C–RFID–3/09
i
registers
Related parts for AT88SC3216CRF-MVB1G
Image
Part Number
Description
Manufacturer
Datasheet
Request
R

Part Number:
Description:
CryptoMemory 32 Kbit
Manufacturer:
ATMEL [ATMEL Corporation]
Datasheet:

Part Number:
Description:
IC EEPROM 32KBIT 1.5MHZ 8SOIC
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
IC EEPROM 32KBIT 1.5MHZ 8DIP
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
IC EEPROM 32KBIT 1.5MHZ 8DIP
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
CRYPTOMEM 32KBIT 16ZONE MOD J TW
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
IC EEPROM 32KBIT 1.5MHZ 8LAP
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
IC EEPROM 32KBIT 1.5MHZ M2J
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
DEV KIT FOR AVR/AVR32
Manufacturer:
Atmel
Datasheet:

Part Number:
Description:
INTERVAL AND WIPE/WASH WIPER CONTROL IC WITH DELAY
Manufacturer:
ATMEL Corporation
Datasheet:

Part Number:
Description:
Low-Voltage Voice-Switched IC for Hands-Free Operation
Manufacturer:
ATMEL Corporation
Datasheet:

Part Number:
Description:
MONOLITHIC INTEGRATED FEATUREPHONE CIRCUIT
Manufacturer:
ATMEL Corporation
Datasheet: